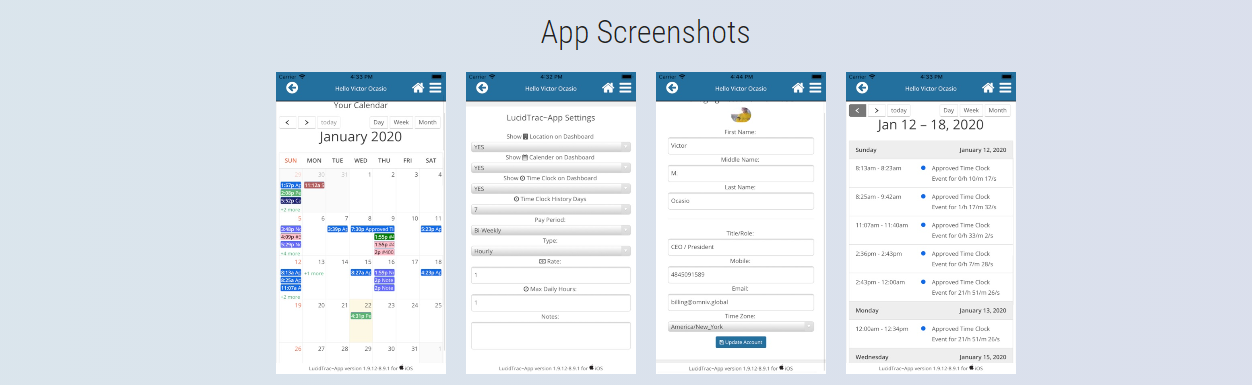
Securing the Future of ERP: Combating Cybersecurity Threats and Boosting Employee Productivity
In today's rapidly evolving digital landscape, businesses face an increasing number of cybersecurity threats. These threats can compromise sensitive data and damage a company's reputation. As a leading ERP software platform, LucidTrac understands the importance of securing your organization's data and ensuring employee productivity. In this blog post, we will discuss the various security measures and strategies you can adopt to protect your business from security threats while enhancing employee productivity.
Understanding the Cybersecurity Landscape
Cybersecurity threats are constantly evolving, posing significant risks to businesses and organizations. Hacking is a prevalent threat, in which unauthorized individuals or groups exploit vulnerabilities in computer systems or networks to access sensitive information, disrupt operations, or manipulate data. Data breaches occur when unauthorized individuals gain access to confidential information, often with the intent to use it for nefarious purposes, such as identity theft or financial fraud. These breaches can have severe consequences, including financial losses, legal penalties, and damage to a company's reputation.
Zero-day vulnerabilities are another major cybersecurity threat that businesses must be aware of. These vulnerabilities are previously unknown software or hardware flaws that can be exploited by hackers before the software vendor becomes aware of them and releases a patch. Zero-day attacks can be particularly dangerous, as they often go undetected, allowing hackers to infiltrate systems and compromise sensitive data. In some cases, these attacks may also enable cybercriminals to gain control over critical infrastructure, leading to devastating consequences for businesses and their customers.
Staying informed about Common Vulnerabilities and Exposures (CVE) is crucial for businesses to ensure the security of their systems and networks. CVE is a publicly accessible database that provides a standardized way to identify and describe known security vulnerabilities in software and hardware. By keeping track of CVE information, businesses can be proactive in applying patches and updates to their systems, reducing the risk of falling victim to cyberattacks that exploit known vulnerabilities.
Furthermore, being aware of CVEs allows businesses to assess the security of their third-party software and hardware providers. By evaluating the history of vulnerabilities and patch management for these providers, businesses can make more informed decisions about which vendors to work with, minimizing potential security risks. Additionally, staying informed about CVEs helps businesses develop a better understanding of the current cybersecurity landscape, enabling them to implement more effective security strategies and policies to protect their assets and customers from potential threats.
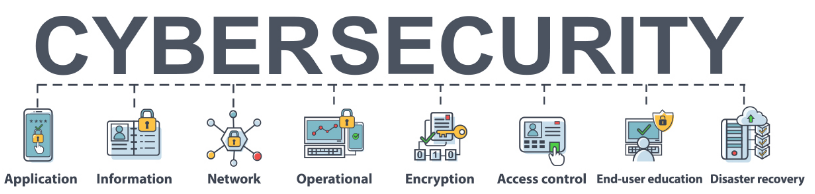
Strengthening Software and Information Security
Software security and information security play crucial roles in protecting businesses from cybersecurity threats. Software security focuses on ensuring that applications and systems are designed, developed, and maintained in a way that minimizes vulnerabilities and prevents unauthorized access. This involves implementing secure coding practices, conducting regular security testing, and applying patches and updates promptly. By securing software, businesses can reduce the risk of cyberattacks that exploit weaknesses in applications and systems, thereby safeguarding their critical data and operations.
Information security, on the other hand, encompasses a broader range of measures to protect sensitive data, both digital and physical, from unauthorized access, disclosure, modification, or destruction. This includes implementing various security controls, such as access controls, firewalls, intrusion detection and prevention systems, and security policies and procedures. By ensuring robust information security, businesses can protect their valuable intellectual property, customer data, and other sensitive information from theft, misuse, and unauthorized access, thereby maintaining trust with their customers and partners and complying with data protection regulations.
Multi-factor authentication (MFA) and data encryption are essential security measures that can significantly enhance the protection of a business's digital assets. MFA is an authentication method that requires users to provide two or more separate forms of identification before granting access to a system or application. This can include something the user knows (such as a password), something the user has (such as a physical token or smartphone), or something the user is (such as a fingerprint or facial recognition). By implementing MFA, businesses can dramatically reduce the risk of unauthorized access, as attackers are less likely to be able to provide multiple forms of identification.
Data encryption is another vital security measure that involves converting readable data into an unreadable format, which can only be deciphered with the appropriate decryption key. By encrypting sensitive data, businesses can ensure that even if unauthorized individuals manage to gain access to their systems, the information remains unreadable and useless to the attacker. Data encryption can be applied both in transit, such as when data is transmitted over a network, and at rest, such as when data is stored on a server or device. Implementing data encryption helps businesses protect their sensitive information from theft or eavesdropping and ensures compliance with data protection regulations, thereby bolstering their overall security posture.

Utilizing Cloud Services for Enhanced Security and Productivity
Cloud hosting services like Google Cloud, Amazon Web Services (AWS), and Microsoft Azure offer numerous advantages for businesses seeking to optimize their digital infrastructure. One of the primary benefits is scalability, as cloud services allow businesses to quickly and easily scale their computing resources up or down based on demand, without the need for significant upfront investment in hardware or infrastructure. This flexibility enables companies to manage their resources more efficiently and adapt to changing business needs.
Another advantage of using cloud hosting services is cost savings. By leveraging shared resources and economies of scale, these providers can offer competitive pricing for their services, allowing businesses to save on hardware, maintenance, and energy costs. Furthermore, the pay-as-you-go pricing model ensures that businesses only pay for the resources they use, reducing wastage and allowing for more accurate budgeting. Cloud hosting services also provide enhanced security and reliability, as they employ state-of-the-art security measures and backup systems to protect data and maintain uptime. This ensures that businesses can trust their cloud providers to keep their data secure and their systems operational, even in the face of potential threats or disruptions.
Cloud computing plays a pivotal role in enhancing a business's infrastructure, data protection, and disaster recovery planning. By utilizing cloud-based infrastructure, businesses can access cutting-edge technologies and services without the need for substantial capital investment or in-house expertise. This allows for more agile and efficient deployment of IT resources, enabling businesses to stay ahead of the competition and adapt to changing market conditions.
In terms of data protection, cloud computing providers often employ advanced security measures such as encryption, intrusion detection, and access controls to safeguard the data stored on their platforms. This means that businesses can benefit from the expertise and resources of their cloud providers to maintain the confidentiality, integrity, and availability of their data, without having to manage all aspects of security themselves. Additionally, cloud providers often offer robust backup and redundancy options, ensuring that data is protected against loss or corruption.
Disaster recovery planning is another area where cloud computing can provide significant benefits. By leveraging the cloud's distributed nature, businesses can create offsite backups and store critical data in multiple geographic locations, reducing the risk of data loss due to localized disasters. Cloud-based disaster recovery solutions also enable rapid recovery of systems and data, minimizing downtime and ensuring business continuity. This can be particularly valuable for businesses that rely on their digital infrastructure to deliver essential services and maintain customer trust.

Employee Productivity: The Role of ERP Solutions
Enterprise Resource Planning (ERP) solutions like LucidTrac can significantly boost employee productivity by streamlining operations and simplifying the management of various business processes. By integrating all essential functions of a business, such as finance, HR, sales, and inventory, into a single unified system, ERP solutions can eliminate redundancies and minimize manual data entry. This helps to reduce the chances of errors, save time, and enable employees to focus on more value-added tasks.
Workflow management is another critical aspect where ERP solutions can make a difference. With features like task automation and process optimization, LucidTrac can help businesses establish clear, efficient workflows that eliminate bottlenecks and enhance overall productivity. Real-time data synchronization is another key advantage of using ERP systems like LucidTrac . By ensuring that all departments have access to up-to-date information, these systems can improve collaboration, enable informed decision-making, and reduce the risk of miscommunication or data-related errors.
User-friendly interfaces and customizable features play a vital role in enhancing employee engagement and efficiency when using ERP solutions. An intuitive, easy-to-use interface ensures that employees can quickly learn to navigate the system and perform their tasks without significant difficulty. This reduces the learning curve and allows employees to become productive more rapidly, while also minimizing the need for extensive training and support.
Customizable features, on the other hand, enable businesses to tailor the ERP solution to their unique needs and preferences. By allowing organizations to configure the system according to their specific requirements, ERP solutions like LucidTrac can improve efficiency and ensure that employees can access the tools and functionalities they need to perform their tasks effectively. Customization can also help businesses adapt to changing market conditions or organizational goals, ensuring that their ERP system remains relevant and useful over time. Ultimately, user-friendly interfaces and customizable features contribute to higher employee satisfaction, better adoption rates, and a more efficient, productive workforce.

Creating a Culture of Security and Continuous Improvement
Building a strong security culture within an organization is crucial for mitigating cybersecurity risks and protecting valuable business assets. A security culture is an environment in which all employees are aware of the importance of cybersecurity, understand their roles and responsibilities in safeguarding sensitive data, and actively participate in maintaining a secure workplace. By fostering a security-conscious mindset among employees, organizations can significantly reduce the likelihood of security incidents caused by human error, such as falling for phishing attacks or inadvertently disclosing sensitive information.
Creating a strong security culture requires ongoing training, communication, and reinforcement. Employees should be educated about the latest threats, best practices for handling sensitive data, and the organization's security policies and procedures. Regular security awareness training can help ensure that employees stay informed about potential risks and know how to respond to potential threats. Leadership should also set an example by emphasizing the importance of security and demonstrating a commitment to maintaining a secure working environment. By fostering a culture of security, organizations can enhance their overall cybersecurity posture and reduce the risk of breaches or data loss.
Failure, while often perceived negatively, can serve as a valuable learning opportunity that encourages resilience and growth. When individuals and organizations experience setbacks or failures, they have the opportunity to analyze what went wrong, identify the underlying causes, and develop strategies for improvement. This process of reflection and analysis can lead to the development of new skills, a deeper understanding of challenges, and ultimately, a stronger and more effective approach to problem-solving.
Embracing failure as a learning opportunity can also foster a growth mindset within an organization, where employees are encouraged to take risks, experiment, and learn from their mistakes. This mindset can lead to increased innovation, as employees feel empowered to explore new ideas and strategies without the fear of failure holding them back. By viewing setbacks as opportunities for growth rather than purely negative experiences, organizations can develop a more resilient workforce that is better equipped to face challenges and adapt to change. In the long run, embracing failure as a learning opportunity can contribute to the overall success and development of both individuals and organizations.
Vendor Management and Ensuring Compliance
Vendor management plays a crucial role in mitigating security threats, as vendors and third-party service providers can introduce vulnerabilities into an organization's IT ecosystem. By effectively managing vendor relationships, organizations can ensure that their suppliers adhere to the necessary security standards and practices, reducing the risk of security breaches and data loss.
A comprehensive vendor management strategy involves assessing the security posture of potential vendors, continuously monitoring their performance, and conducting regular audits to ensure compliance with the organization's security requirements. This process helps organizations identify any potential weaknesses in their supply chain, allowing them to address risks before they become major issues. Additionally, a robust vendor management strategy should include clear expectations and contract provisions regarding data security, incident response, and liability in the event of a breach. By prioritizing vendor management, organizations can minimize security threats and maintain the integrity of their IT infrastructure.
Compliance with data protection regulations and industry standards is essential for organizations that handle sensitive data, as it demonstrates a commitment to safeguarding customer and employee information. Adhering to these regulations and standards, such as the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), or the Payment Card Industry Data Security Standard (PCI DSS), ensures that organizations implement robust security measures to protect the privacy and confidentiality of the data they process.
Failure to comply with data protection regulations can result in significant financial penalties, reputational damage, and loss of customer trust. In addition to these consequences, non-compliance can also expose organizations to greater security risks, as they may not have implemented the necessary safeguards to protect sensitive information from unauthorized access or misuse. By complying with data protection regulations and industry standards, organizations can demonstrate their commitment to data privacy and security, while also mitigating the risk of costly breaches and legal ramifications.

Maximizing the Benefits of ERP Solutions for Business Growth
Effective implementation of ERP solutions offers numerous advantages for businesses, including cost reductions, better decision-making, and improved customer experience. By consolidating various business processes into a single, integrated system, ERP solutions can help organizations streamline operations, eliminate redundancies, and reduce manual tasks, leading to significant cost savings.
With real-time data synchronization and centralized access to information, ERP systems enable better decision-making by providing accurate, up-to-date data that can inform strategic planning, resource allocation, and operational adjustments. As a result, businesses can quickly respond to changes in market conditions, customer demands, and internal processes, enhancing overall efficiency and agility.
An integrated ERP system can also greatly improve the customer experience by automating processes such as order processing, invoicing, and customer support. This leads to faster response times, more accurate order fulfillment, and a seamless experience across multiple touchpoints. By streamlining these processes, businesses can deliver a higher level of service, ultimately boosting customer satisfaction and loyalty.
Here are some examples of businesses that have successfully leveraged ERP solutions for growth and success:
-
Cisco Systems: Cisco, a leading global technology company, implemented an ERP system to streamline its complex supply chain operations. The Oracle's Enterprise Resource Planning (ERP) solution enabled the company to manage and track inventory, production, and order fulfillment more efficiently, resulting in reduced costs, improved customer service, and increased sales.
-
Rolls-Royce: Luxury automaker Rolls-Royce adopted SAP S/4HANA Cloud ERP solution to consolidate its various business processes and gain better visibility into its operations. The system allowed the company to improve its production planning, resource allocation, and customer service, contributing to its continued growth and success in the competitive automotive market.
-
Nestlé: The world's largest food and beverage company, Nestlé, turned to SAP AG ERP system to integrate its global operations and improve efficiency across its vast supply chain. The implementation of the ERP solution enabled Nestlé to standardize processes, improve data accuracy, and optimize resource utilization, leading to cost savings and enhanced decision-making capabilities.
These examples demonstrate how organizations across various industries, from large enterprises to small businesses, can leverage ERP solutions to drive growth, improve efficiency, and deliver an exceptional customer experience. While the mentioned examples are from large companies, it's worth noting that ERP platforms like LucidTrac are affordable and adaptable enough even for a single person to use, making them accessible to businesses of all sizes.
In Conclusion:
In the age of ever-increasing cybersecurity threats, businesses must prioritize security and employee productivity to stay competitive and maintain customer trust. By adopting robust security measures, such as multi-factor authentication, data encryption, and vendor management, organizations can effectively mitigate potential security risks and ensure the protection of sensitive information.
Utilizing cloud services like Google Cloud, AWS, and Azure can provide businesses with enhanced infrastructure, data protection, and disaster recovery planning, ensuring seamless operations and business continuity in the face of unforeseen challenges. Cloud services also offer scalability and cost-efficiency, allowing businesses to grow and adapt to changing market conditions.
Implementing comprehensive ERP solutions like LucidTrac can significantly boost employee productivity by streamlining operations, workflow management, and real-time data synchronization. With user-friendly interfaces and customizable features, ERP systems can enhance employee engagement and efficiency, leading to better decision-making and improved customer experience.
By fostering a strong security culture within the organization and embracing failure as a learning opportunity, businesses can encourage resilience, innovation, and growth. In conclusion, prioritizing security and employee productivity, leveraging cloud services, and implementing effective ERP solutions like LucidTrac are essential for businesses to thrive in today's complex and rapidly evolving digital landscape.
Share this Blog Post: https://lcdtrc.link/blcq96o
In Case you Missed It - Seach by Tags!

Visit our YouTube channel at https://youtube.com for help and videos about the #LucidTrac Platform.

Introducing the #softwareKing Motivational Mobile App Section: Unleash Your Self Motivational Power
At LucidTrac ERP, we are proud to announce the launch of an exciting new section within our Mobile App: #softwareKing. Designed to inspire, empower, and uplift, #softwareKing brings you an exclusive collection of Daily Motivational Videos, curated to fuel your ambition and drive your success.
With the #softwareKing section, we believe that motivation knows no bounds. That's why we have made these inspirational videos accessible to everyone, without the need for an account or any subscription fees. Simply download our app, and immerse yourself in a world of powerful messages and transformative insights.
Compare LucidTrac to other online platforms
To help you get a better understanding of your needs by comparing LucidTrac to other online ERP / SaaS platforms.
LucidTrac offers a comprehensive solution to streamline all of your business operations.
With its fully customizable features, LucidTrac allows you to tailor the platform to meet the specific needs of your business.

Compare LucidTrac to
Zoho CRM

Compare LucidTrac to
Zendesk CRM

Compare LucidTrac to
Freshdesk CRM

Compare LucidTrac to
Salesforce CRM

Compare LucidTrac to
Monday CRM

Compare LucidTrac to
HubSpot CRM

Compare LucidTrac to
Keap CRM

Compare LucidTrac to
Sugar CRM

Compare LucidTrac to
SherpaDesk CRM
| Comparing Feature | LucidTrac | Zoho CRM | Zendesk CRM | Freshdesk CRM | Salesforce CRM | Monday CRM | HubSpot CRM | Keap CRM | Sugar CRM | SherpaDesk CRM |
| Price | $300 Unlimited Users | $49 Avg/Per User | $149 Avg/Per User | $109 Avg/Per User | $125 Avg/Per User | $99 Avg/Per User | $99 Avg/Per User | $49 Avg/Per User | $45 Avg/Per User | $49 Avg/Per User |
| Free Trial | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| Support 24/7 | Yes | Yes | No | No | No | No | No | No | No | No |
| Developer API | Yes | Yes | No | Yes | No | No | No | No | No | Yes |
| Dashboards | Yes | Yes | No | Yes | No | Yes | No | No | Yes | No |
| To-Dos | Yes | Yes | No | Yes | No | Yes | No | No | Yes | Yes |
| Products & Assets | Yes | Yes | No | Yes | No | Yes | No | No | Yes | Yes |
| User Roles | Yes | Yes | No | Yes | No | Yes | No | No | Yes | No |
| 2FA (Two-Factor Authentication) | Yes | Yes | No | Yes | No | Yes | No | No | Yes | No |
| Multi Method Importing | Yes | Yes | No | No | No | Yes | No | No | No | No |
| Documents & Templates | Yes | No | No | No | No | No | No | No | No | No |
| iOS/Android Apps | Yes | Yes | No | No | No | No | No | No | No | Yes |
| Statistics & Reporting | Yes | Yes | No | Yes | No | No | No | No | No | Yes |
| Storage | 500G Base Node | 1G | 1G | 1G | 1G | 1G | 1G | 1G | 1G | - |
| Monthly Payments | Yes | Yes | No | Yes | No | No | No | No | No | Yes |
| Campaigns | Yes | Yes | No | Yes | No | No | No | No | No | No |
| Exporting Services | Yes | Yes | Yes | Yes | No | No | Yes | No | Yes | No |
| Emailing | Yes | Yes | No | Yes | No | No | No | No | No | No |
| SMS Inbound/Outbound | Yes | Yes | No | Yes | No | No | No | No | No | No |
| Voice Calling Inbound/Outbound | Yes | Yes | No | Yes | No | No | No | No | No | No |
| IVR Services | Yes | Yes | No | Yes | No | No | No | No | No | No |
| Google Calendar/Authentication | Yes | Yes | No | Yes | No | No | No | No | No | No |
| Service Tickets / Time Tracking | Yes | Yes | No | Yes | No | No | No | No | No | Yes |
| Email to Service Ticket Services | Yes | Yes | yes | Yes | No | No | No | No | No | Yes |
| Time Clock / Payroll Exporting | Yes | No | No | No | No | No | No | No | No | No |
| Networking / IP & Host Management | Yes | No | No | No | No | No | No | No | No | No |
| Web Forms / Landing Pages | Yes | Yes | No | Yes | No | No | Yes | No | No | No |
| Invoice/Payment Collections Tools | Yes | No | No | No | No | No | No | No | No | No |
| Customized Programming | Yes | No | No | No | No | No | No | No | No | No |

Mr. Kevin Johnson
BlueSpruce Consulting Services, LLC.

Mr. Craig Stonaha
CEO Laughing Rock Technologies, LLC.
John Adams
President/CEO - RDI

Dennis Canlas
USCR
Brian Gomez
Gomez Check Cashing

Mr. Michael Graziano
Prime Time Mortgage Corp.

Mr. Nicholas Tannous
NWT Enterprises Ltd - San Juan, Trinidad and Tobago

Mrs. Cynthia Garrett
Berks ENT - Reading PA